MY-ASSIGNMENTEXPERT™可以为您提供 ics.uci.edu CS167 Cryptography密码学的代写代考和辅导服务!

CS167课程简介
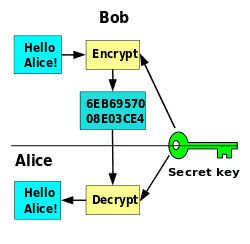
Encryption is a very complicated process in general, but you can simplify it by:
encrypting each character in the file independently
using a bitwise operator or operators to scramble each character separately
store the password (encrypted!) in the output file so that it can be compared with the password typed on the command line for decryption.
make sure your encryption technique uses bitwise operators, and is reversible. i.e. there is a way of recovering the character from the encrypted form reliably for all possible characters (the ASCII set). A very easy technique is to use the complement operator ~.
don’t put the password in any shape or form in your source code – the user of the program should have complete responsibility for it.
File processing is chapter 11; the bitwise operators are section 10.9; handling command line arguments is section 14.4.
Prerequisites
Deliverables
The problem statement, description and TDSR design diagram.
The completed source code.
A sample input file and the same file after encryption and decryption. The listings should be identical. There is no need to show the encrypted file since it should bear no resemblance to the input and will probably contain non-printing characters anyway.ments, or any incorrect ones.
CS167 Cryptography HELP(EXAM HELP, ONLINE TUTOR)
The 4th century Indian text, Kama Sutra, proposes, among other things, a method for secret writing where each letter is paired with another and each occurrence of a letter in a document is replaced by its mate. For example, we could pair $(A, V),(B, N),(C, E),(D, F),(E, C),(F, D)$, and so on, so that every “A” is replaced by “V” and every “V” is replaced by “A”, every “B” is replaced by “N” and every “N” is replaced by “B”, etc.
a. Give an example encryption using a Kama Sutra cipher.
a. Example encryption using Kama Sutra cipher: Plain text: THE QUICK BROWN FOX JUMPS OVER THE LAZY DOG Key: (A,V),(B,N),(C,E),(D,F),(E,C),(F,D),(G,S),(H,T),(I,K),(J,Y),(K,I),(L,X),(M,Z),(N,B),(O,P),(P,O),(Q,U),(R,W),(S,G),(T,H),(U,Q),(V,A),(W,R),(X,L),(Y,J),(Z,M)
Encrypted text: GVS VSNGL YIRHV UFA WKTXN IGVS XZBP AQM
b. How many possible keys are there for the Kama Sutra cipher?
b. Number of possible keys: There are 26 letters in the English alphabet, so there are 26 possible letters to pair each letter with. The first letter can be paired with any of the remaining 25 letters, the second with any of the remaining 24, and so on. This gives a total of 25 × 24 × 23 × … × 2 × 1 possible keys, which is equal to 26! (26 factorial). This is approximately equal to $4 \times 10^{26}$ possible keys.
c. What is the security of the Kama Sutra cipher with respect to the four kinds of attacks that can be done on a cryptosystem?
c. Security of the Kama Sutra cipher: The Kama Sutra cipher is a simple substitution cipher, which means that it is vulnerable to several attacks:
- Ciphertext-only attack: Since each letter is always replaced by the same letter, the frequency distribution of the letters in the encrypted text will be the same as in the original text. Therefore, an attacker can use frequency analysis to determine the most common letter in the encrypted text, which is likely to correspond to the letter “E” in the original text, and then work from there to determine the rest of the key.
- Known plaintext attack: If an attacker knows the correspondence between some plaintext and ciphertext letters, they can use that knowledge to determine the key. For example, if an attacker knows that “FOX” encrypts to “YIRHV”, they can use this information to determine that (F,D), (O,P), and (X,Z) are part of the key.
- Chosen plaintext attack: If an attacker can choose the plaintext to be encrypted, they can use that knowledge to determine the key. For example, if an attacker chooses the plaintext to be a repeated letter, they can determine which letter corresponds to itself in the key.
- Chosen ciphertext attack: If an attacker can choose the ciphertext, they can use that knowledge to determine the key. For example, if an attacker chooses the ciphertext to be a repeated letter, they can determine which letter corresponds to itself in the key.
MY-ASSIGNMENTEXPERT™可以为您提供UNIVERSITY OF ILLINOIS URBANA-CHAMPAIGN MATH2940 linear algebra线性代数课程的代写代考和辅导服务! 请认准MY-ASSIGNMENTEXPERT™. MY-ASSIGNMENTEXPERT™为您的留学生涯保驾护航。