如果你也在 怎样代写网络安全network security这个学科遇到相关的难题,请随时右上角联系我们的24/7代写客服。网络安全network security是一套技术,通过防止各种潜在威胁进入或在网络中扩散,来保护公司基础设施的可用性和完整性。
网络安全network security一个网络安全架构是由保护网络本身和在网络上运行的应用程序的工具组成。有效的网络安全策略采用了可扩展和自动化的多道防线。每个防御层都执行一套由管理员决定的安全策略。
my-assignmentexpert™ 网络安全network security作业代写,免费提交作业要求, 满意后付款,成绩80\%以下全额退款,安全省心无顾虑。专业硕 博写手团队,所有订单可靠准时,保证 100% 原创。my-assignmentexpert™, 最高质量的网络安全network security作业代写,服务覆盖北美、欧洲、澳洲等 国家。 在代写价格方面,考虑到同学们的经济条件,在保障代写质量的前提下,我们为客户提供最合理的价格。 由于统计Statistics作业种类很多,同时其中的大部分作业在字数上都没有具体要求,因此网络安全network security作业代写的价格不固定。通常在经济学专家查看完作业要求之后会给出报价。作业难度和截止日期对价格也有很大的影响。
想知道您作业确定的价格吗? 免费下单以相关学科的专家能了解具体的要求之后在1-3个小时就提出价格。专家的 报价比上列的价格能便宜好几倍。
my-assignmentexpert™ 为您的留学生涯保驾护航 在数学Mathematics作业代写方面已经树立了自己的口碑, 保证靠谱, 高质且原创的网络安全network security代写服务。我们的专家在数学Mathematics代写方面经验极为丰富,各种网络安全network security相关的作业也就用不着 说。
我们提供的网络安全network security及其相关学科的代写,服务范围广, 其中包括但不限于:
非线性方法 nonlinear method functional analysis
变分法 Calculus of Variations
数学代写|网络安全作业代写network security代考|Secrecy vs. Integrity
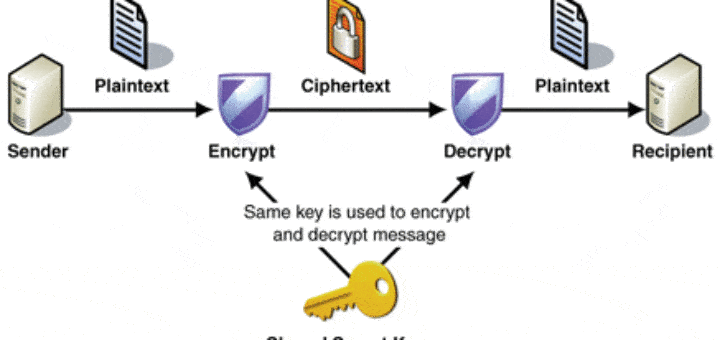
A basic goal of cryptography is to enable parties to communicate securely. But what does “secure communication” entail? In Chapter 3 we showed how it is possible to achieve secrecy; that is, we showed how encryption can be used to prevent a passive eavesdropper from learning anything about messages sent over an open channel. However, not all security concerns are related to secrecy, and not all adversaries are limited to passive eavesdropping. In many cases, it is of equal or greater importance to guarantee message integrity (or message authentication) against an active adversary who can inject messages on the channel or modify messages in transit. We consider two motivating examples corresponding to the settings of Figures $1.1$ and 1.2, respectively.
Imagine first a user communicating with her bank over the Internet. When the bank receives a request to transfer $\$ 1,000$ from the user’s account to the account of some other user $X$, the bank has to consider the following:
- Is the request authentic? That is, did the user in question really issue this request, or was the request issued by an adversary (perhaps $X$ itself) who is impersonating the legitimate user?
- Assuming a transfer request was issued by the legitimate user, is the request received by the bank exactly the same as what was sent by that user? Or was, e.g., the transfer amount modified as the request was sent across the Internet?
Note that standard error-correction techniques do not suffice for the second concern. Error-correcting codes are only intended to detect and recover from “random” errors that affect a small portion of the transmission, but they do nothing to protect against a malicious adversary who can choose exactly where to introduce an arbitrary number of changes.
数学代写|网络安全作业代写network security代考|Encryption vs. Message Authentication
Just as the goals of secrecy and message integrity are different, so are the techniques and tools for achieving them. Unfortunately, secrecy and integrity are often confused and unnecessarily intertwined, so let us be clear up front: encryption does not (in general) provide any integrity, and encryption should not be assumed to ensure message authentication unless it is specifically designed with that purpose in mind (something we will return to in Section 5.2).
One might mistakenly think that encryption solves the problem of message authentication. (In fact, this is a common error.) This is due to the fuzzy, and incorrect, reasoning that since a ciphertext completely hides the contents of the message, an adversary cannot possibly modify an encrypted message in any meaningful way. Despite its intuitive appeal, this reasoning is completely false. We illustrate this point by showing that all the encryption schemes we have seen thus far do not provide message integrity.
网络安全作业代写
数学代写|网络安全作业代写NETWORK SECURITY代考|SECRECY VS. INTEGRITY
密码学的一个基本目标是使各方能够安全地通信。但是“安全通信”意味着什么?在第 3 章中,我们展示了如何实现保密。也就是说,我们展示了如何使用加密来防止被动窃听者了解有关通过开放通道发送的消息的任何信息。然而,并不是所有的安全问题都与保密有关,也不是所有的对手都局限于被动窃听。在许多情况下,保证消息完整性具有同等或更大的重要性这r米和ss一种G和一种在吨H和n吨一世C一种吨一世这n针对可以在通道上注入消息或修改传输中的消息的活跃对手。我们考虑两个与图的设置相对应的激励示例1.1和 1.2,分别。
首先想象一个用户通过 Internet 与她的银行进行通信。当银行收到转账请求时$1,000从用户的帐户到其他用户的帐户X,银行必须考虑以下几点:
- 请求是否真实?也就是说,有问题的用户是否真的发出了这个请求,或者这个请求是由对手发出的p和rH一种ps$X$一世吨s和lF谁在冒充合法用户?
- 假设转账请求是由合法用户发出的,银行收到的请求与该用户发送的请求是否完全相同?或者,例如,当请求通过 Internet 发送时,转账金额是否被修改?
请注意,标准纠错技术不足以解决第二个问题。纠错码仅用于检测影响一小部分传输的“随机”错误并从中恢复,但它们并不能防止恶意对手可以准确选择在何处引入任意数量的更改。
数学代写|网络安全作业代写NETWORK SECURITY代考|ENCRYPTION VS. MESSAGE AUTHENTICATION
正如保密和消息完整性的目标不同一样,实现这些目标的技术和工具也不同。不幸的是,保密性和完整性经常被混淆和不必要地交织在一起,所以让我们先澄清一下:加密不一世nG和n和r一种l提供任何完整性,并且不应假定加密以确保消息身份验证,除非它是专门为该目的而设计的s这米和吨H一世nG在和在一世llr和吨在rn吨这一世n小号和C吨一世这n5.2.
有人可能会错误地认为加密解决了消息认证的问题。一世nF一种C吨,吨H一世s一世s一种C这米米这n和rr这r.这是由于模糊且不正确的推理,即由于密文完全隐藏了消息的内容,攻击者不可能以任何有意义的方式修改加密消息。尽管它具有直观的吸引力,但这种推理是完全错误的。我们通过展示到目前为止我们看到的所有加密方案都没有提供消息完整性来说明这一点。
数学代写|网络安全作业代写network security代考 请认准UprivateTA™. UprivateTA™为您的留学生涯保驾护航。

