数学代写| Breaking the Enigma Codes 代考
离散数学在计算领域有广泛的应用,例如密码学、编码理论、 形式方法, 语言理论, 可计算性, 人工智能, 理论 数据库和软件的可靠性。 离散数学的重点是理论和应用,而不是为了数学本身而研究数学。 一切算法的基础都是离散数学一切加密的理论基础都是离散数学
编程时候很多奇怪的小技巧(特别是所有和位计算相关的东西)核心也是离散数学
其他相关科目课程代写:组合学Combinatorics集合论Set Theory概率论Probability组合生物学Combinatorial Biology组合化学Combinatorial Chemistry组合数据分析Combinatorial Data Analysis
my-assignmentexpert愿做同学们坚强的后盾,助同学们顺利完成学业,同学们如果在学业上遇到任何问题,请联系my-assignmentexpert™,我们随时为您服务!
离散数学代写
The Enigma codes were used by the Germans during the second world war for the secure transmission of naval messages to their submarines. These messages contained top-secret information on German submarine and naval activities in the Atlantic, and the threat that they posed to British and Allied shipping.
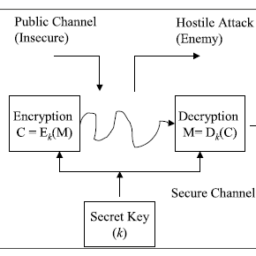
The codes allowed messages to be passed secretly using encryption, and this meant that any unauthorised inteception was meaningless to the Allies. The plaintext (i.e., the original message) was converted by the Enigma machine (Fig. 10.2) into the encrypted text, and these messages were then transmitted by the German military to their submarines in the Atlantic, or to their bases throughout Europe.
The Enigma machine was invented in 1918 and generated a polyalphabetic substitution cipher which the Germans believed to be unbreakable. A letter was typed in German into the machine, and electrical impulses through a series of rotating wheels and wires produced the encrypted letter which was lit up on a panel above the keyboard. The recipient typed the received message into his machine and the decrypted message was lit up letter by letter above the keyboard. The rotors and wires of the machine could be configured in many different ways, and during the war the cipher settings were changed at least once a day. The odds against anyone breaking the Enigma machine without knowing the setting were $150 \times 10^{18}$ to 1 .
The British code and cipher school was relocated from London to Bletchley Park (Fig. 10.3) at the start of the second world war. It was located is in the town of Bletchley near Milton Keynes (about fifty miles north west of London). It was commanded by Alistair Dennison and was known as Station X, and several thousands were working there during the second world war. The team at Bletchley Park Allied war effort.Polish cryptanalysts did important work in breaking the Enigma machine in the early $1930 \mathrm{~s}$, and they constructed a replica of the machine. They passed their knowledge on to the British and gave them the replica just prior to the German invasion of Poland. The team at Bletchley built upon the Polish work, and the team included Alan Turing $^{1}$ (Fig. 10.4) and other mathematicians.
The code-breaking teams worked in various huts in Bletchley park. Hut 6 focused on air force and army cyphers, and hut 8 focused on naval cyphers. The deciphered messages were then converted into intelligence reports, with air force and army intelligence reports produced by the team in hut 3 , and naval intelligence reports produced by the team in hut 4. The raw material (i.e., the encreted messages) to be deciphered came from wireless intercept stations dotted around Britain, messages, and sent them to Bletchley park to be deciphered and analysed.
Turing devised a machine to assist with breaking the codes (an idea that was originally proposed by the Polish cryptanalysts). This electromechanical machine was known as the bombe (Fig. 10.5), and its goal was to find the right settings of
${ }^{1}$ Turing made fundamental contributions to computing, including the theoretical Turing machine.
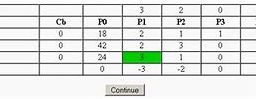
$10.2$ Breaking the Enigma Codes Fig. $10.5$ Replica of bombe
165
and the time required to determine the settings on the Enigma machime, and it and the time required to determine the settings on the Enigma machine, and it became the main tool for reading the Enigma traftic during the war. The bombe was tological device designed in 1938 by the Polish cryptologist, Marian Rejewski.
A standard Enigma machine employed a set of rotors, and each rotor could be in any of 26 positions. The bombe tried each possible rotor position and applied a test. The test eliminated almost all of the positions and left a smaller number of cases to be dealt with. The test required the cryptologist to have a suitable “crib”: i.e., a section of ciphertext for which he could guess the corresponding plaintext.
For each possible setting of the rotors, the bombe employed the crib to perform a chain of logical deductions. The bombe detected when a contradiction had occurred and it then ruled out that setting and moved onto the next. Most of the possible settings would lead to contradictions and could then be discarded. This would leave only a few settings to be investigated in detail.
The Government Communication Headquarters (GCHQ) was the successor of Bletchley Park, and it opened after the war. The site at Bletchley park was then used for training purposes.
The codebreakers who worked at Bletchley Park were required to remain silent about their achievements until the mid-1970s when the wartime information was declassified. ${ }^{2}$ The link between British Intelligence and Bletchley Park came to an end in the mid-1980s.
It was decided in the mid-1990s to restore Bletchley Park, and today it is run as a museum by the Bletchley Park Trust.

二战期间,德国人使用 Enigma 代码将海军信息安全地传输到他们的潜艇。这些信息包含有关德国潜艇和海军在大西洋活动的绝密信息,以及它们对英国和盟军航运构成的威胁。
这些代码允许使用加密方式秘密传递消息,这意味着任何未经授权的窃听对盟军来说都是毫无意义的。明文(即原始消息)由 Enigma 机器(图 10.2)转换为加密文本,然后这些消息由德国军方传输到他们在大西洋的潜艇或他们在整个欧洲的基地。
Enigma 机器是在 1918 年发明的,它产生了一种多字母替换密码,德国人认为这种密码是牢不可破的。在机器中输入一个德语字母,通过一系列旋转轮和电线的电脉冲产生加密的字母,该字母在键盘上方的面板上点亮。收件人将收到的消息输入他的机器,解密的消息在键盘上方一个字母一个字母地亮起。机器的转子和电线可以以多种不同的方式进行配置,在战争期间,密码设置至少每天更改一次。任何人在不知道设置的情况下破坏 Enigma 机器的几率是 $150 \times 10^{18}$ to 1 。
第二次世界大战开始时,英国密码和密码学校从伦敦迁至布莱切利公园(图 10.3)。它位于米尔顿凯恩斯附近的布莱切利镇(伦敦西北约五十英里)。它由 Alistair Dennison 指挥,被称为 X 站,二战期间有数千人在那里工作。 Bletchley Park Allied 战争努力的团队。波兰密码分析家在 1930 年初的 \mathrm{~s}$ 中为破解 Enigma 机器做了重要的工作,他们构建了机器的复制品。他们将他们的知识传给了英国人,并在德国入侵波兰之前给了他们复制品。 Bletchley 的团队以波兰的工作为基础,团队成员包括 Alan Turing $^{1}$(图 10.4)和其他数学家。
破译团队在布莱切利公园的各种小屋中工作。小屋 6 专注于空军和陆军密码,小屋 8 专注于海军密码。然后将破译的消息转换为情报报告,其中空军和陆军情报报告由 3 号小屋小组制作,海军情报报告由 4 号小屋小组制作。要破译的原材料(即加密的消息)来自英国各地的无线拦截站,消息,并将它们发送到布莱切利公园进行破译和分析。
图灵设计了一台机器来帮助破解密码(这个想法最初是由波兰密码分析家提出的)。这种机电机器被称为炸弹(图 10.5),它的目标是找到正确的设置
${ }^{1}$ 图灵对计算做出了根本性的贡献,包括理论上的图灵机。
$10.2$ 破解 Enigma Codes 图 $10.5$ 炸弹复制品
165
以及确定Enigma机器上的设置所需的时间,以及确定Enigma机器上的设置所需的时间,它成为战争期间阅读Enigma traftic的主要工具。该炸弹是波兰密码学家玛丽安·雷耶夫斯基于 1938 年设计的逻辑装置。
标准的 Enigma 机器采用一组转子,每个转子可以位于 26 个位置中的任何一个。炸弹尝试了每个可能的转子位置并进行了测试。这次测试几乎消除了所有的职位,只剩下少量的案件需要处理。该测试要求密码学家有一个合适的“婴儿床”:即他可以猜测相应明文的密文部分。
对于转子的每种可能设置,炸弹都使用婴儿床进行一系列逻辑推理。炸弹在发生矛盾时检测到,然后排除了该设置并转移到下一个设置。大多数可能的设置会导致矛盾,然后可以被丢弃。这将只留下一些需要详细调查的设置。
政府通讯总部(GCHQ)是布莱切利公园的继任者,战后开放。布莱切利公园的场地随后被用于培训目的。
在布莱切利公园工作的密码破译者被要求对他们的成就保持沉默,直到 1970 年代中期战时信息被解密。 ${ }^{2}$ 英国情报局和布莱切利公园之间的联系在 1980 年代中期结束。
1990 年代中期决定修复布莱切利公园,如今它由布莱切利公园信托基金作为博物馆运营。
图论代考
自然数 $\mathbb{N}$ 由数字 $\{1,2,3, \ldots\}$ 组成。整数 $\mathbb{Z}$ 由 $\{\ldots-2,-1,0,1,2, \ldots\}$ 组成。有理数 $\mathbb{Q}$ 由 $\left\{{ }^{p} /_{q}\right.$ 形式的所有数字组成,其中 $p$ 和 $q$ 是整数,$ \left.q \neq 0\right\}$。实数 $\mathbb{R}$ 被定义为有理数收敛序列的集合,它们是有理数的超集。它们包含有理数和无理数。复数 $\mathbb{C}$ 由 $\{a+bi$ 形式的所有数字组成,其中 $a, b \in \mathbb{R}$ 和 $i=\sqrt{-} 1\}美元。 毕达哥拉斯三元组(图 3.2)是满足毕达哥拉斯方程 $x^{2}+y^{2}=z^{2}$ 的三个整数的组合。有无数个这样的三元组,这种三元组的一个例子是 $3,4,5$,因为 $3^{2}+4^{2}=5^{2}$。 毕达哥拉斯学派发现了音乐和数字之间的数学关系,他们的哲学是数字隐藏在从音乐到科学和自然的一切事物中。这导致了他们的哲学,即“一切都是数字”。
数学代写| DISCRETE MATHEMATICS代考 请认准UprivateTA™. UprivateTA™为您的留学生涯保驾护航。
抽象代数代考
抽象代数就是一门概念繁杂的学科,我们最重要的一点我想并不是掌握多少例子。即便是数学工作者也不会刻意记住Jacobson环、正则环这类东西,重要的是你要知道这门学科的基本工具和基本手法,对概念理解了没有,而这一点不需要用例子来验证,只需要看看你的理解和后续概念是否相容即可。
矩阵论代考matrix theory
数学,矩阵理论是一门研究矩阵在数学上的应用的科目。矩阵理论本来是线性代数的一个小分支,但其后由于陆续在图论、代数、组合数学和统计上得到应用,渐渐发展成为一门独立的学科。
密码学代考
密码学是研究编制密码和破译密码的技术科学。 研究密码变化的客观规律,应用于编制密码以保守通信秘密的,称为编码学;应用于破译密码以获取通信情报的,称为破译学,总称密码学。 电报最早是由美国的摩尔斯在1844年发明的,故也被叫做摩尔斯电码。
- Cryptosystem
- A system that describes how to encrypt or decrypt messages
- Plaintext
- Message in its original form
- Ciphertext
- Message in its encrypted form
- Cryptographer
- Invents encryption algorithms
- Cryptanalyst
- Breaks encryption algorithms or implementations
编码理论代写
编码理论(英语:Coding theory)是研究编码的性质以及它们在具体应用中的性能的理论。编码用于数据压缩、加密、纠错,最近也用于网络编码中。不同学科(如信息论、电机工程学、数学、语言学以及计算机科学)都研究编码是为了设计出高效、可靠的数据传输方法。这通常需要去除冗余并校正(或检测)数据传输中的错误。
编码共分四类:[1]
数据压缩和前向错误更正可以一起考虑。