MY-ASSIGNMENTEXPERT™可以为您提供 utexas.edu CS167 Cryptography密码学的代写代考和辅导服务!
这是德克萨斯州大学奥斯汀分校密码学课程的代写成功案例。

CS346课程简介
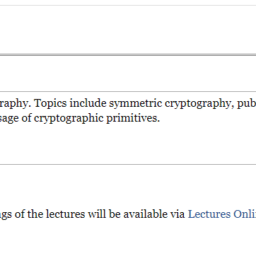
This course provides an introduction to modern cryptography. Topics include symmetric cryptography, public-key cryptography, digital signatures, key agreement, and zero-knowledge proofs. We will also cover proper usage of cryptographic primitives.
Location: RLP 1.104
Time: Tuesday, Thursday, 2:00pm-3:30pm
The default delivery of this course is in person. Recordings of the lectures will be available via Lectures Online. If you are not able to make it to lecture or are feeling unwell, please watch the recordings offline.
Prerequisites
Canvas: We will use Canvas, which includes links to Ed Discussion (for announcements and class discussions and Gradescope for assignment submission and grading.
Ed Discussion: We will use Ed Discussion for class discussions and for sending out course announcements. If you have a question about the course material or course logistics, please post it on Ed Discussion instead of emailing the course staff directly. You should be automatically added to the Ed Discussion site via Canvas once the semester starts.
Lectures Online: Recordings of the lectures will be available via Lectures Online after the lecture (if available). You can also access Lectures Online via Canvas.
Gradescope: Homework submissions will be handled via Gradescope. You should be automatically enrolled in the course via Canvas once the semester starts.
Homework: Please see the Course Organization and Policies page for details on how to format and submit your homeworks as well as the collaboration policy for the course.
CS346 Cryptography HELP(EXAM HELP, ONLINE TUTOR)
Exercise 1. Let $e=n=21825283495649$ be a public key of the RABIN cryptosystem. Decrypt $c \in \mathbb{Z} / n \mathbb{Z}$ encoded as
$$
111000101110111110000111010101010101111000
$$
in binary digits.
Exercise 2. Complete the proof of Theorem 6.1 .8 by proving: Let $p$ and $q$ be distinct odd primes and $t \in \mathbb{N}$ with
$$
\operatorname{ord}{(\mathbb{Z} /(p-1) \mathbb{Z},+)}(t)=\operatorname{ord}{(\mathbb{Z} /(q-1) \mathbb{Z},+)}(t)=2^k .
$$
Then
$$
\operatorname{ord}{(\mathbb{Z} /(p-1) \mathbb{Z},+)}(x t) \neq \operatorname{ord}{(\mathbb{Z} /(q-1) \mathbb{Z},+)}(t)
$$
for half of all pairs $(x, y) \in \mathbb{Z} /(p-1) \mathbb{Z} \times \mathbb{Z} /(q-1) \mathbb{Z}$.
Exercise 3. Prove the first statement of Remark 6.4 .1 and the last statement of Remark 6.4 .2 :
(1) The BLUM-GOLDWASSER cryptosystem does not satisfy the security model IND-CCA2.
(2) If the assumptions QR and SQROOT are equally strong, then the BLUMGOLDWASSER does not satisfy the security model ASYMMETRY-CCA2.
Exercise 4. Let $\left(n, e_1\right)$ and $\left(n, e_2\right)$ be two public RSA-keys, $x<n$ a plaintext, and $c_i=\varepsilon_{\left(n, e_i\right)}(x)$ the corresponding ciphertexts. Show that if $e_1$ and $e_2$ are coprime ${ }^1$ then $x$ can be easily computed using $c_1, c_2$, and the two public keys.
Exercise 5. Time-Memory Trade-offs $\left[12\right.$ points]. Let $F:{0,1}^n \times{0,1}^n \rightarrow{0,1}^n$ be a block cipher (i.e., a PRP). Let $G:{0,1}^{2 n} \times{0,1}^n \rightarrow{0,1}^n$ be the function $G\left(k_1 | k_2, x\right):=F\left(k_2, F\left(k_1, x\right)\right.$ ). Given a pair $(x, y)$, your goal is to find some key $k=k_1 | k_2$ such that $y=G\left(k_1 | k_2, x\right)$. A brute force search over all possible keys $k \in{0,1}^{2 n}$ would take time $2^{2 n} \cdot$ poly $(n)$. Show that using $2^n \cdot$ poly $(n)$ space, there is an algorithm that recovers some key $k$ in $2^n \cdot$ poly $(n)$ time. Prove the correctness and running time of your algorithm. Your solution to this problem is an example of a time-memory trade-off that is often possible in cryptanalysis.
MY-ASSIGNMENTEXPERT™可以为您提供 UTEXAS.EDU CS167 CRYPTOGRAPHY密码学的代写代考和辅导服务!