MY-ASSIGNMENTEXPERT™可以为您提供 sydney MATH2088 Cryptography密码学的代写代考和辅导服务!
这是悉尼大学 密码学课程的代写成功案例。
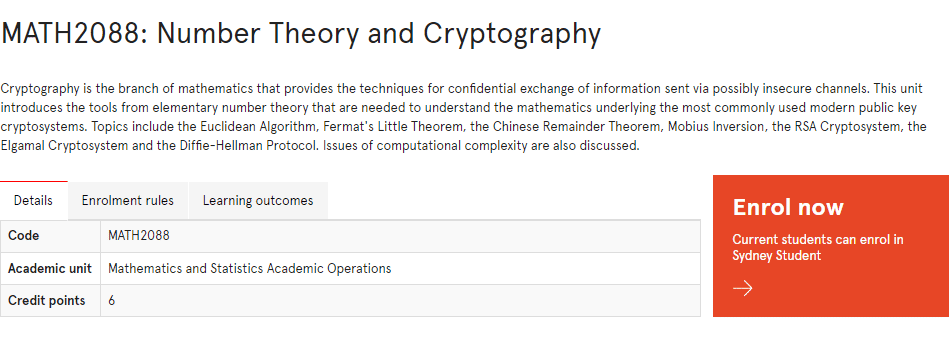
MATH2088课程简介
Cryptography is the branch of mathematics that provides the techniques for confidential exchange of information sent via possibly insecure channels. This unit introduces the tools from elementary number theory that are needed to understand the mathematics underlying the most commonly used modern public key cryptosystems. Topics include the Euclidean Algorithm, Fermat’s Little Theorem, the Chinese Remainder Theorem, Mobius Inversion, the RSA Cryptosystem, the Elgamal Cryptosystem and the Diffie-Hellman Protocol. Issues of computational complexity are also discussed.
Prerequisites
At the completion of this unit, you should be able to:
- LO1. understand and use the basic terminology of number theory and cryptography
- LO2. carry out simple number-theoretic computations either with a calculator or using MAGMA
- LO3. apply standard number-theoretic algorithms
- LO4. understand and use some classical and number-theoretic cryptosystems
- LO5. apply standard methods to attack some classical cryptosystems
- LO6. understand the theory underlying number-theoretic algorithms and cryptosystems, including the general properties of primes, prime factorisation, modular arithmetic, divisors and multiplicative functions, powers and discrete logarithms.
MATH2088 Cryptography HELP(EXAM HELP, ONLINE TUTOR)
(3 points) Edit encrypt.c so that it implements DES encryption in electronic codebook (ECB) mode. This files should be submitted as encrypt_ecb.c. Encrypt the two included image files.
(3 points) The skeleton intentionally avoids encrypting the BMP file’s header so you can use standard software to inspect the encrypted data. Open the two encrypted files in your favorite image editor. (We used the GIMP.) Was the encryption effective? Explain the difference between the two encrypted files.
(3 points) Find a small (under 1MB uncompressed) image file that would be more effectively encrypted using a block cipher in ECB mode. Explain your choice of image. What sorts of attacks is this scheme vulnerable to?
Convert the image to an uncompressed (not RLE encoded) 24-bit BMP format and encrypt it. Name the files plain.bmp and crypt.bmp and submit them.
(4 points) Edit encrypt.c so that it implements DES encryption in cipher block chaining (CBC) mode. This files should be submitted as encrypt_cbc.c. For this exercise, a block of all 0 ‘s may be used as the initialization vector. Encrypt the two original image files and view the result.
How do the results differ when CBC is used instead of ECB? Briefly state why that is the case.
(5 points) Alice and Bob are using public keys $\left(e_1, N_1\right),\left(e_2, N_2\right)$ respectively. Suppose you are informed that their RSA moduli $N_1, N_2$ are not relatively prime. How would you break the security of their subsequent communication? It is sufficient to show that you can get $\phi\left(N_1\right)$ and $\phi\left(N_2\right)$.
(Extra Credit, 5 points). Show that an attacker who discovers the private key $(d, N)$ for a public key $(e=3, N)$, can efficiently factor $N=p . q$. Recall, we compute $e d=1(\bmod \phi(N))$, such that $d<\phi(N)$.
MY-ASSIGNMENTEXPERT™可以为您提供 sydney MATH2088 Cryptography密码学的代写代考和辅导服务!