MY-ASSIGNMENTEXPERT™可以为您提供 sydney MATH2088 Cryptography密码学的代写代考和辅导服务!
这是悉尼大学 密码学课程的代写成功案例。

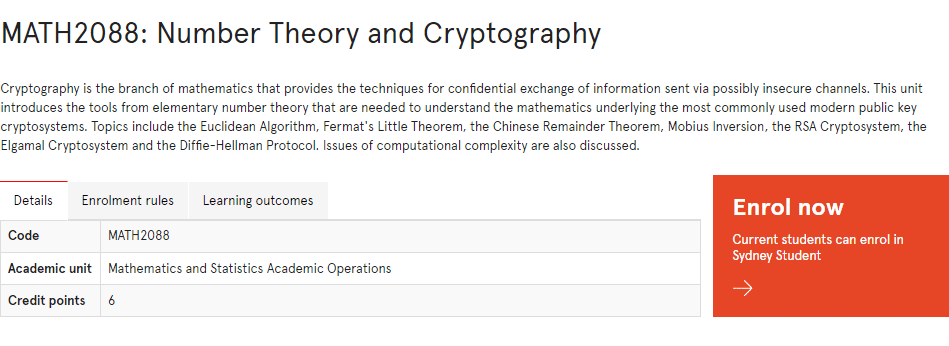
MATH2088课程简介
Cryptography is the branch of mathematics that provides the techniques for confidential exchange of information sent via possibly insecure channels. This unit introduces the tools from elementary number theory that are needed to understand the mathematics underlying the most commonly used modern public key cryptosystems. Topics include the Euclidean Algorithm, Fermat’s Little Theorem, the Chinese Remainder Theorem, Mobius Inversion, the RSA Cryptosystem, the Elgamal Cryptosystem and the Diffie-Hellman Protocol. Issues of computational complexity are also discussed.
Prerequisites
At the completion of this unit, you should be able to:
- LO1. understand and use the basic terminology of number theory and cryptography
- LO2. carry out simple number-theoretic computations either with a calculator or using MAGMA
- LO3. apply standard number-theoretic algorithms
- LO4. understand and use some classical and number-theoretic cryptosystems
- LO5. apply standard methods to attack some classical cryptosystems
- LO6. understand the theory underlying number-theoretic algorithms and cryptosystems, including the general properties of primes, prime factorisation, modular arithmetic, divisors and multiplicative functions, powers and discrete logarithms.
MATH2088 Cryptography HELP(EXAM HELP, ONLINE TUTOR)
(7 points) Suppose Alice has to sign a contract with Mallory using an RSA signature where, the signature is computed by $s=(h(m))^d \bmod N(d$ is Alice’s private key). Assume that the hash function is an idealized, perfectly random hash function $h(x)$, i.e $h$ is selected uniformly at random from all functions mapping ${0,1}^*$ to ${0,1}^k$, and $h$ is publicly known. Mallory has managed to find 40 distinct places where he can make a slight change in the contract: adding a space at the end of line, adding a comma, replacing with equivalent words (like replacing “agreed to pay” with “is obliged to pay”), etc. Surely, Alice does not object any such minor change in the contract and is willing to sign a contract with any of these minor changes.
(2 points) How many possible versions of the contract can Mallory generate that Alice would be willing to sign?
(3 points ) Mallory creates a fraudulent contract reflecting a substantial increase in amount that Alice owes to Mallory. He computes the hash of the fraudulent contract as $h(f)$ and finds a version of the good contract that hashes to the same value $h(f)$. What is a minimum safe output size for the hash function (i.e $k=$ ?) to make these collisions unlikely? (An approximate answer with appropriate reasoning is acceptable. You need not show any calculations to get ‘ $k$ ‘.)
(2 point) What can Mallory do by finding such a collision, to force Alice to pay an increased amount in court?
Solution. For each slight change, Mallory can choose to use it or not. There are 40 such changes. So, Mallory can generate $2^{40}$ contracts that Alice will be willing to sign.
Solution. Given that Mallory was able to compute $2^{40}$ different versions of the good contract, we compute how likely is it that one of them hashes to the hash value of his fraudulent contract. Let the size of the hash output be ‘ $k$ ‘ bits.
The probability that the first good version hashes to the fraudulent one, is $\left(1 / 2^k\right)$. The probability that the first good version does not hash to the same hash as the fraudulent one is $\left(1-\left(1 / 2^k\right)\right)$. Therefore, the probability that none of the $2^{40}$ good contracts hash to the same value as the hash of the fraudulent case, is $\left(1-1 / 2^k\right)^{2^{40}}$. From this it follows that the probability that atleast one of the $2^{40}$ versions has the same hash as the fraudulent one is $1-\left(1-1 / 2^k\right)^{20}$.
You can choose how unlikely the event of such collisions should be. For $k=40$, this probability becomes $63 \%$. For $k=41$, this becomes nearly $40 \%$. For $k>50$, the probability is less than $0.1 \%$.
Solution. Mallory finds a version out of the $2^{40}$ good contracts, that hashes to the same value as the fraudulent contract. He asks Alice to sign the version of the good contract, and Alice complies. Since the hash values are same, the signatures for the fraudulent contract and the good version will be same. Mallory presents the fraudulent contract appended with the signature of the good version in court, to claim that Alice had signed the fraudulent version.
(5 points) Recall from class that in an RSA signature scheme, the signature is computed by $s=(h(m))^d \bmod N$, where d is the private key. Consider an naive revised scheme where the signature is computed as $s^{\prime}=m^d \bmod N$ instead. Show that it is possible to forge signatures for some messages in the latter (revised) scheme.
Hint : Suppose Alice uses the latter (revised) scheme to sign two contracts $m_1, m_2$, generating signatures $s_1^{\prime}, s_2^{\prime}$ respectively. Construct an attack from $s_1^{\prime}, s_2^{\prime}$.
Solution. Suppose a bank signs messages $m_1$ and $m_2$, to generate signatures $s_1^{\prime}$ and $s_2^{\prime}$. An attacker can forge the bank’s signature for the message $m_1 \cdot m_2$, by simply multiplying the given signatures $s_1^{\prime} s_2^{\prime} \bmod N$.
Reasoning about Code. (8 points)
The (poorly written) function StringEncrypt, shown in Figure 1, encrypts the input string and returns the encrypted string. The function is not memory safe, and does not behave correctly on all inputs.
(4 points) Spot all the bugs that could cause the program to execute an unsafe memory operation.
Solution. input and key are not checked to be non-NULL. length +4 could lead to integer overflow. encrypted should be checked for non-NULL, after being assigned the return value of malloc. Buffer overflow for encrypted and input by one byte in the loop – writing past the buffer size by 1 . Also, in general, you should state what are sizes of size_t and other data types on the target architecture to make sure that there are no implicit cast bugs.
( 4 points) Introduce the additional necessary checks to ensure that all memory operations in the function execute safely, without changing the intended functionality. You may refer to the man pages for the documentation of the $\mathrm{C}$ library function interface. You should show the checks inlined in the code above at the right places where they should appear; you should annotate your inserted code as C comments to demarcate it from original code.
Solution. Inlined as comments in figure 1 ..
MY-ASSIGNMENTEXPERT™可以为您提供 sydney MATH2088 Cryptography密码学的代写代考和辅导服务!